Before You Begin
AppConfig² requires administrator consent for successful onboarding. Please ensure you have the following prerequisites before starting:
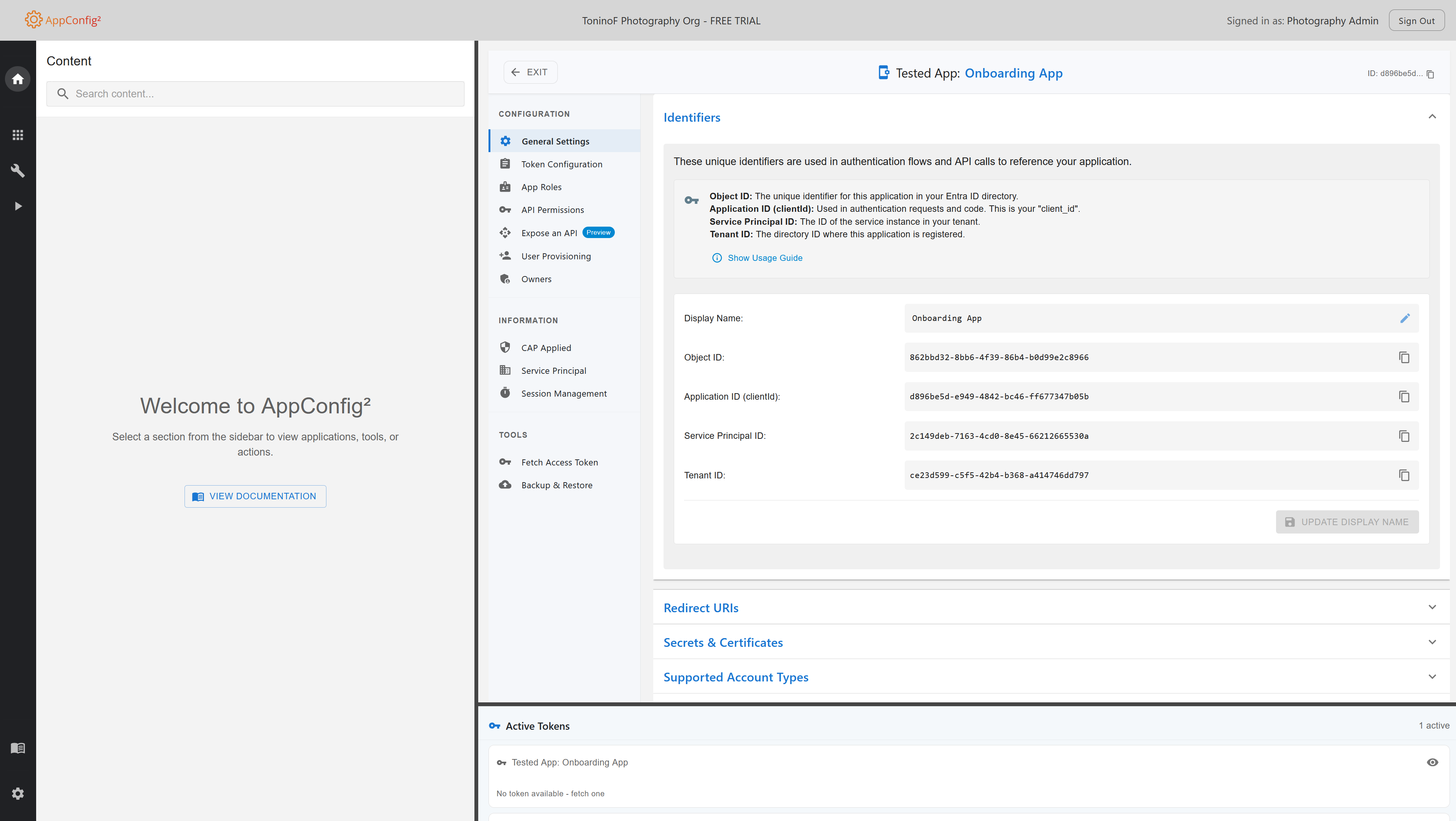
Onboarding Process
Step 1: Sign In
Sign in with your Microsoft Entra ID account. You'll be directed to Microsoft's authentication page.

Step 2: Administrator Consent
After signing in, you'll be prompted to grant administrator consent for the required permissions. You must be signed in with an administrator account for this step.
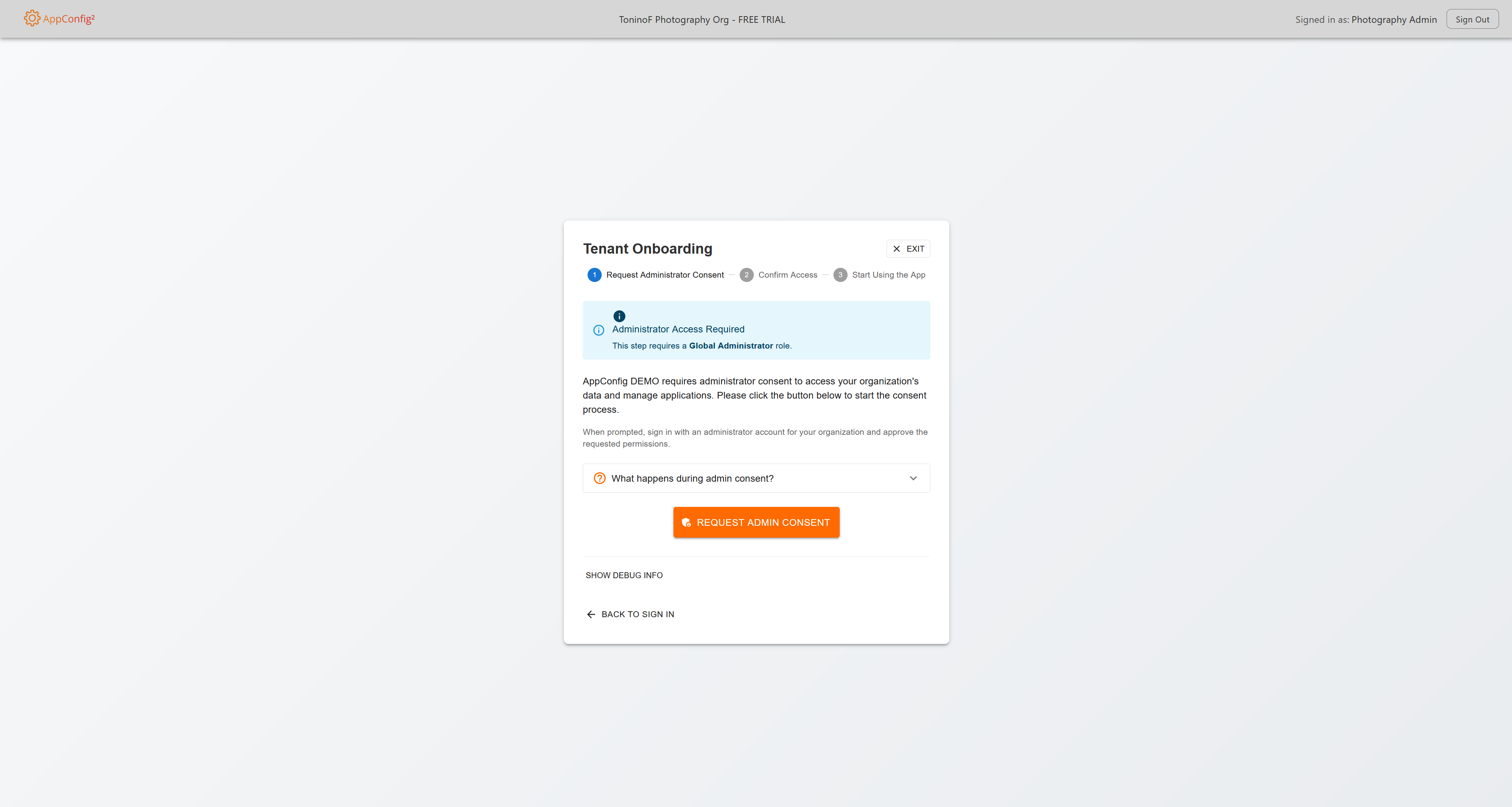
Step 3: Access the Application
Once consent is granted, you'll have full access to all features of AppConfig².